How to check if your personal data has been compromised online


There seems to be an endless number of personal data leaks that happens every year, and it is not uncommon to discover that your information is freely available for sale on the Dark Web. Learn how to check whether your personal information or password has been compromised.
Apple and Google's password managers do offer the option to check whether your account(s) has/have been listed in known leaks from time to time, doing so against logins and passwords that have been saved in iOS/Safari and Android/Chrome, respectively.
Despite this, not all users take advantage of this feature, simply ignore it, or simply store the account information on the cloud. That's where Have I Been Pwned comes in.

The site compares publicly leaked databases - having over 11 billion accounts at the time of publishing, with an email address or phone number that is provided by the user.
Jump to:
- How to check if you're on any leaked lists
- What to do if your data has been leaked
- How to lessen damage in the future
- Facebook breach exposed data of 500 million accounts
How to check if your personal data has been leaked
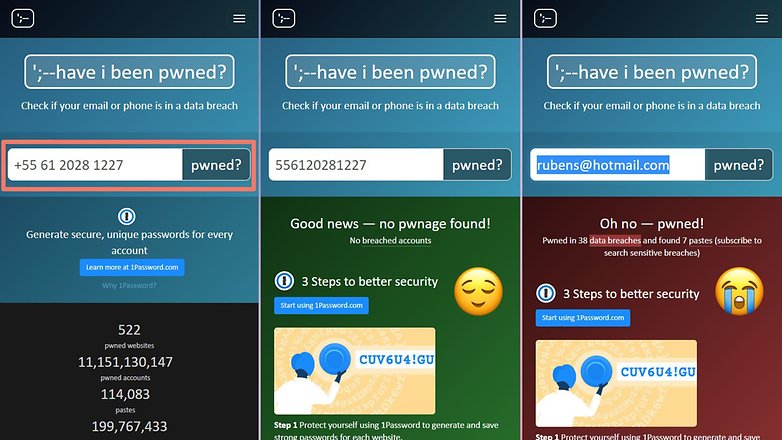
- Go to haveibeenpwned.com.
- Enter an email address or phone number following the international format (with the country code and country code) in the text field.
- Click the pnwed? button.
If your data has not been compromised in any way, then the site will display the message, "Good news - no pwnage found!".
On the other hand, if your login information was found in a leaked database, the message displayed will be "Oh no — pwned!" followed by a list of known leaks in the form of "Pwned in [number of] data breaches and found [number of] pastes.
The list of leaked databases specifies what kind of information is included - e-mail, password, physical address, IP addresses, date of birth, and phone number for example - and a brief summary of how the data was obtained and leaked.
What to do if you are a victim of a data breach
Based on the results shown in Have I Been Pwned, the first thing to do is to eliminate repeating passwords that have been used on numerous sites. While nearly everyone is guilty of this, it is highly recommended to use unique and hard-to-guess combinations.
Once you have done the necessary, always check on whether payment information has been stored, including your debit or credit card numbers. Also, do inquire with your credit card company or issuing bank whether there are any recent abnormal transactions. If there were, then what are the recommended remedial steps that can be taken?
Apart from that, there is very little else that you can do as your data is already publicly available. Another security measure that you can take is to change the answers in your password recovery systems which relies on your leaked data, such as "In which city were you born?", which is a laborious process but a necessary evil.
How to avoid falling for new password leaks
The only way to guarantee that your password does not get leaked out is not to create any user accounts or registrations in the first place. Even deleting as much personal information as possible from current services doesn't guarantee anything, as some leaks do include data that should have been removed by companies in the first place.
To minimize any fallout from future leaks, we continue to echo the often-repeated advice of using unique and hard-to-guess passwords. Password suggestion tools that are built into Chrome and Safari (Edge and Firefox as well) will help you avoid simple combinations like "123456," as well as synchronize passwords across multiple connected devices.
Oh, and please enable two-factor authentication whenever possible.
Data of 500 million Facebook accounts leaked
In April 2021, information of over half a billion Facebook logins began circulating on the Internet. According to the social network itself, this data was not obtained from its systems being hacked, but rather, by a tool that scoured the platform and took advantage of any loose ends and loopholes.
The company says it closed access to the feature used in September 2019, and recommends using the Privacy Verification tool that is readily available on the social network.
Leaked information includes names, gender, date of birth, location, relationships, and work statuses, which are normally associated with phone numbers and, in some cases, email addresses.
As if the leak was not devastating enough, a new scouring tool was released two weeks later, revealing how one can obtain emails associated with user accounts. Parallel to this, Belgian website DataNews sighted an internal Facebook email that directed its public relations teams to attribute this data breach to a "broad industry issue," in a poor attempt to downplay the previous snafu.
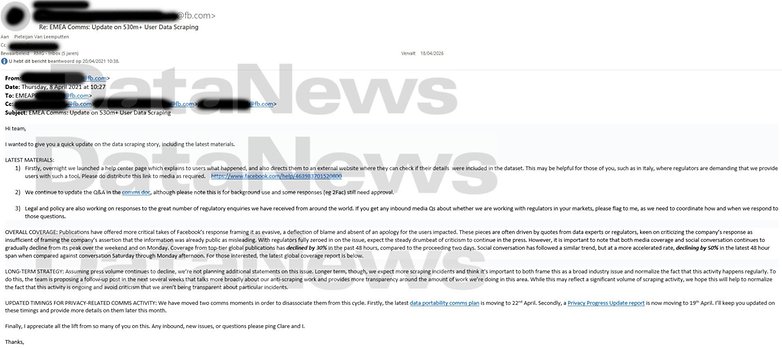
Despite the attempt to manipulate public opinion, the fact remains that other services experienced major data leaks in the same month, including LinkedIn and Clubhouse. Unfortunately, this is not the last time that we will see personal information circulating around freely, even with the necessary security mechanisms in place or your country's personal data privacy.
Source: DataNews


















sound good.