7 ways to stop the NSA spying on your nude pics

Some of you may have seen the British comedian John Oliver interviewing Edward Snowden recently for his late night program Last Week Tonight. Oliver interviewed some people on the street to demonstrate how little they care about domestic spying programs, but when he asked how they'd feel about the NSA accessing their d*** pics, suddenly things changed. If this bothers you (because it really should), here's how to stop the NSA and other hackers from spying on your Android and all the ''junk'' you've got stored in it.

Get yourself a VPN
A Virtual Private Network is exactly what it sounds like: a private network connection for browsing the internet. VPNs like Hotspot Shield encrypt your incoming and outgoing data, so while it may still be intercepted, it is at least encrypted. Depending on the strength of your VPN it might just be enough to outsmart NSA analysts and other hackers that intercept your data. VPNs can also cover up your IP address, enable HTTPS security and more to keep your identity safe.

Browse with Tor
Tor is the secret way to surf the internet. Tor hides your IP address and browsing history from the websites you visit, essentially putting you in ninja mode the whole time you're on the web. While Tor comes in a convenient desktop download, there are also Android app versions like Orbot. Orbot bounces your internet traffic around different global servers, rather than pushing it directly to your destination, so your original location is obfuscated from anyone poking their nose in your business. You might also want to install a supported browser like Orweb or DuckDuckGo.

Manage app permissions
A lot of apps ask for way too many permissions when you install them. Simple apps like games really don't need a permissions list as long as your arm, so be careful when installing new apps. If an app has too much access to your phone and that app's servers are hacked, then all that juicy info it's collecting about you goes straight to the hackers. If you're rooted, you can also install an app like App Ops to keep an eye on and manage the various permissions your installed apps have. Non-rooted versions like Advanced Permission Manager are also worth checking out.
Use airplane mode more often
Airplane Mode isn't just for airplanes, you know. When you turn on Airplane Mode all broadcasting capabilities of your smartphone are disabled. This means that you effectively drop off the radar when you turn it on. If you're sitting on the subway reading cached emails, playing Sudoku or editing pictures on your smartphone, there's no reason to be allowing those apps to constantly send data about you back to their servers (or ply you with ads). Airplane Mode can be used a lot more than you think, making you that much harder to track.
Encrypt your chats and texts
Many instant messenger apps don't use end-to-end encryption. Until recently, Telegram was the most high profile messenger to offer this level of security. WhatsApp recently announced end-to-end encryption as well, bringing the world's largest messaging network into line with the best security available for keeping your chats safe and secure from prying eyes. You can also make use of great encrypted text messaging apps like Whisper Systems' TextSecure.
Turn off GPS and location reporting
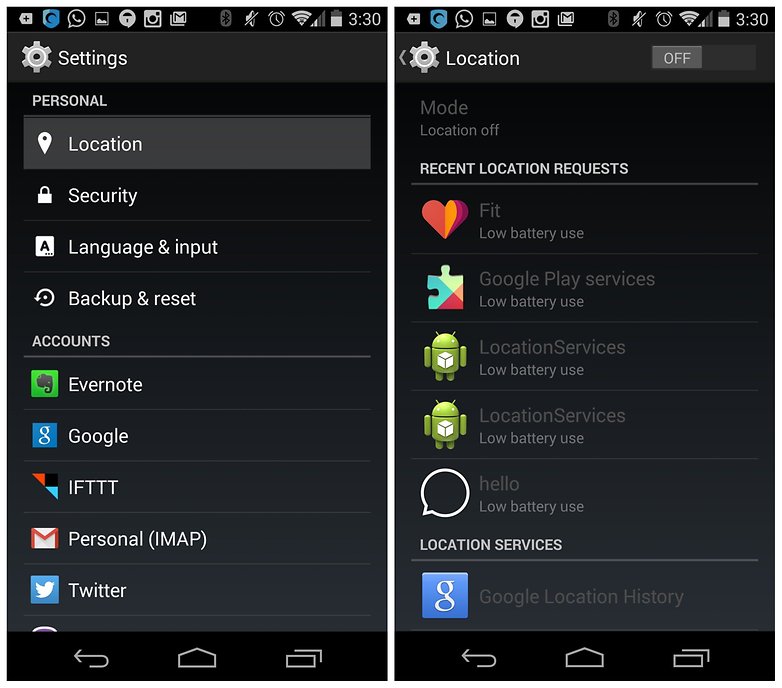
As you probably know, a lot of spying programs rely on knowing exactly where you are. This allows them to specifically track your location throughout the day. While cell towers can provide similar information, they aren't anywhere near as specific as Wi-Fi networks, geo-tagging or GPS data.
Go to your Settings > Location and turn off location reporting if you're at all paranoid about Big Brother tracking your every move. You can also turn off Wi-Fi until you actually need it: why have random networks pinpointing your location unless you're actually using them? You can also turn off geo-tagging in your apps. The most common apps that use this information are camera and photographic apps, social networks and others that like to know your exact location (to then share it with the NSA).
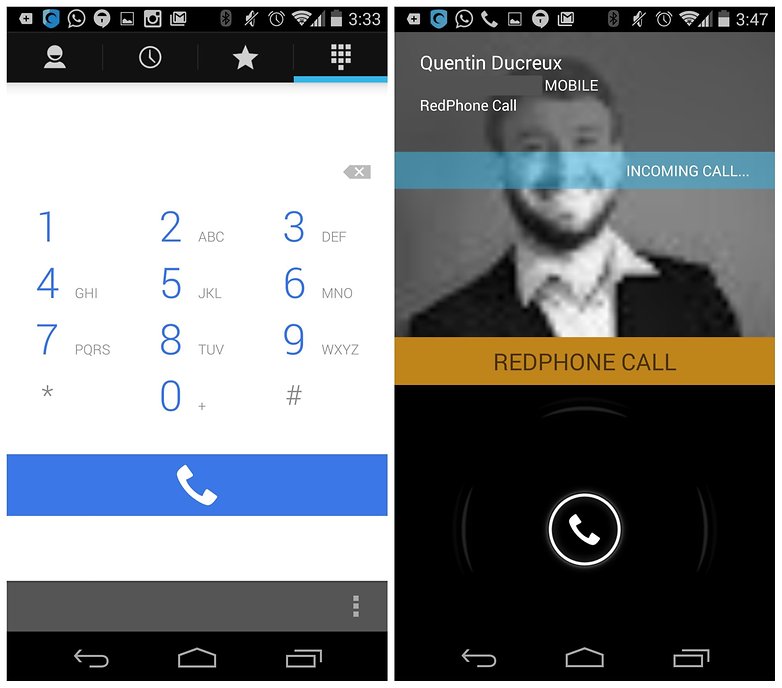
Call privately with Redphone
Encrypting your chats and emails is all fine and good, but what about phone calls: you know, that thing you use your phone for the most? That's where Redphone comes in. Redphone lets you place and receive encrypted voice calls on your smartphone for free. Redphone works just like any other dialer on your phone, but calls are encrypted end-to-end because it uses 4G or Wi-Fi rather than your cellular minutes. If you're serious about keeping your conversations private, this is a worthwhile investment.
What else can I do?
The more you look into it and the more seriously you take your privacy, the easier it is to make choices for the benefit of keeping your identity, data and habits secret. You can do simple things, like switch to an email service like ProtonMail or Hushmail, use more anonymous browsers like DuckDuckGo, use of incognito mode, install ad and pop-up blockers, avoid social networks that are known to hand over your information to anyone with a court order and log out of your accounts unless absolutely necessary.
These small steps add up to a much less visible digital footprint. Anyone trying to track your movements, access your browsing history, profile your associations based on calling activity and geo-location or those trying to steal your identity will have a much harder time of it. If you're serious about not being spied on, you have to take your privacy at least as seriously as those invading it.
How seriously do you take your Android security? What do you do to protect yourself from spying?



















...or don't take nude pictures of yourself (and especially don't store them in the cloud.) No judgement. Just common sense.
Yes. Or use an Android phone... No one using Android had its photos leaked. How Apple got away with that is something I cannot understand.
The fact is that Apple made the upload of pictures an "opt out", so not everyone knew about the pictures taken going to the cloud.
When someone says to me that iOS is safer than Android, I know what to say.
Great article - & I've both invested in one which I learned whilst I already do another - but I must say this for your consideration... Even though this article is helpful, posts like this can give hackers the ability to 'counter' - wherein hackers could now write programs that could get around such tricks... I don't even want to say what sort of programs can be written in detail as same may give hackers ideas - if you follow me - but what I will say is such tips should be shared on a person to person basis(with friends etc)......or something... O.O
I made an account specifically to tell you to shut your stupid mouth. You run the risk of saying something that is intelligent. That would be very misleading to the readers.
Make one thing perfectly clear. Terrorist organizations would be fully fluent in such technologies as pgp i2p and tor.
Anyone who thinks that the NSA are protecting you by spyting on ypu is in actual fact a moron of the highest degree and a willing participant in the progress being made by such groups / governments at erosion of your rights.
I use Orbit (tor) with a Firefox addon it can be a little slower but secure. If you root your phone then orbit can proxy all your apps data as well.
Firefox also has a addon's HTTPS Everywhere that forces non secure sites to use Https, ghostery and cookie clearing. But yeah I agree with prev comment, if the officals have access to the site your visiting then itd game up!
VPNs are useful, but they don't necessarily provide end-to-end encryption. They mostly just change the perceived *source* of your traffic to some other geographic location. Think of trying to hide from the sun by sending traffic through a tunnel. Eventually it has to emerge somewhere to be routed to Facebook or Twitter (for example). The time spent in the tunnel/VPN is safe(r) from prying eyes, but not once it emerges from the tunnel/VPN.
SSL everywhere (e.g. https: to all sites) is probably a better method of protecting traffic from G-men in the middle, assuming, of course, the G-men don't have taps directly into the site you're visiting, which makes the whole exercise futile.
Article is great but i don't think that any normal person would go through all of that just to probably not be spied (he may have never been targeted at the first place). I bought my phone to use it and so i will. i don't care who sees my pictures, videos or whatever. I've hidden the d*** ones in Private Mode so i don't mind the NSA seeing my song album covers at all :P