Pre-installed malware: should you be worried?


Over the past few days, you may have come across a study showing that some Android smartphones come straight out of the box already infected with malware. Initially, this had nothing to do with the manufacturers or the stores that resell the devices, but it could still be risky for users.
Results of the CheckPoint study
The digital security company, Check Point, released the results of a study in which 38 devices, from two different clients, were found to be infected with malware. In both cases, the malware was installed on the device at some unknown point in the supply chain. In other words, some nasty employee has installed malicious software on these smartphones in the time between them being manufactured in the factory and being released for sale.
Following this logic, the malware in question wasn't part of the official ROM provided by the vendor. In six cases, the virus was installed with administer privileges (ROOT access). As a result, the owner of the device wouldn't be able to remove the virus by just restoring factory settings, the famous reset. In order to get rid of the virus they'd have to do an official ROM flash of the device. In other words, reinstall the official manufacturer software.
The threats were found on cell phones from two large companies
Who's responsible for this?
According to the research team, the threats were found in smartphones produced by two major companies which, unfortunately, weren't identified in the CheckPoint study. The article states that one was a "large telecommunications company" and the other a "multinational technology company."
The majority of the malware contained adware (e.g. Loki malware) and info-stealers. Ransomware, which will encrypt all the files on a device and then demand a ransom in return for their decryption, was discovered in one case. This last one is clearly the worst possible one to find, as this could be used to extort money from targeted smartphone users.
The difference between adware and ransomware
| Adware | Ransomware |
|---|---|
| AD= "advertisement" and ware= "software", is any type of automatically run program which shows a large number of ads without the user's permission. | A type of malware which restricts access to the infected system and charges a ransom to reestablish that access. |
Why are Android devices regular targets?
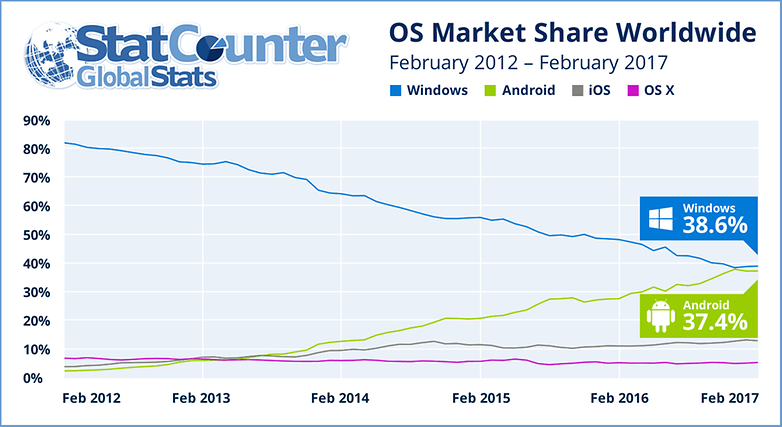
As the most-used mobile platform system in the world, Android is an obvious target for digital crimes. To give you a better idea, according to StatCounter, a website which monitors global web traffic to collate usage statistics for browsers and operating systems, Google is on the verge of passing Windows as having the highest percentage of connected devices. The company's most recent report showed that 37.4% of all online devices used Android against 38.6% using Windows.
Android is a secure operating system
Apart from all that, the number of devices running Google's operating system is huge and is much larger than devices running on the Apple iOS platform.
Additionally, the analysis structure of hosted apps in the Google Play Store has opened it up to some of the more unscrupulous developers currently operating today, as its computer-led selection process does allow malicious apps to be uploaded into the store.
The fact that older versions of Android are still currently in use just increases the system's vulnerability. Google offers monthly updates that contain security patches, but only for those devices running Android 4.4 and up:
"When a moderate or higher severity security vulnerability in AOSP is fixed, we'll notify Android partners of issue details and provide patches for a minimum of the most recent three Android releases. The Android security team currently provides patches for Android versions 4.4 (KitKat), 5.0 (Lollipop), 5.1 (Lollipop MR1), and 6.0 (Marshmallow). This list of backport-supported versions changes with each new Android release", Google.
Don't get me wrong here, Android is still a very secure operating system. Since it's an open source project, many developers are continuously doing system maintenance. However, the fact that it's so popular and it has an absurd fragmentation does make it vulnerable to attack.
List of infected and targeted devices
Despite not having the names of the two large companies cited in the report, we can still refer to the list of infected devices that have been released into the market.
However, it's very important to note that apart from the devices below, this doesn't necessarily mean that all the devices produced by the brands listed below will leave the factory with their security already compromised. According to CheckPoint, some models were tampered with after they had already left the factory.
- Asus Zenfone 2
- Galaxy A5
- Galaxy S7
- Galaxy S4
- Galaxy Note Edge
- Galaxy Note 2
- Galaxy Note 3
- Galaxy Note 4
- Galaxy Note 5
- Galaxy Note 8
- Galaxy Tab S2
- Galaxy Tab 2
- Lenovo S90
- Lenovo A850
- LG G4
- Oppo N3
- Oppo R7 plus
- Vivo X6 plus
- Xiaomi Mi 4i
- Xiaomi Redmi
- ZTE x500ZTE x500vivo
The strange thing is, three days after the study was published, Google Nexus devices were removed from the list without any further explanation. Were the devices removed due to an error in the primary analysis? Were they taken off because Google asked? Despite my best efforts, I wasn't able to confirm anything with CheckPoint's Research Development Team.
Spying: a problem in today's society
The findings of this study raises a number of concerns about the security of mobile devices, but spying and using technology to steal data with the aim of extortion are both key concerns beyond the smartphone market.
Recently, Wikileaks published its "Biggest ever leak of secret CIA documents". According to the group, the 8,761 documents from "Vault 7" contain "several hundred million lines of code" and demonstrates how the agency is able to spy on any smartphone running Android, iOS or Windows.
In other words, CIA agents are introducing viruses which, just as an example, can give them access to a smartphone's microphone, even when it's not connected. This allows agency hackers access to millions of conversations all over the world.
In the end, providing you have the requisite knowledge and access, it's possible to intercept the distribution of a device and manipulate the system so a government agency or criminal gang can have complete control. This has happened in the past when the Chinese manufacturer, Xiaomi, was accused of sending user data from their smartphones to China.
At the time, the Redmi Note was continuously trying to connect to an IP address in Beijing. Here the device would try to connect even when the cloud service had been disabled. Worse than this, the problem persisted even after users installed the latest official version of Android. Xiaomi denied any involvement in the case.
Some time later G Data researchers, a German cyber security company, discovered that the Chinese smartphone, Generic Star N9500, contained the same error. The malware, UUpay.D, had been pre-installed on these devices. It was stealing data and sending it to a Chinese IP address.
As was the case with the Xiaomi smartphone, the malware program couldn't be removed with the factory reset. This security breach from N9500 would allow anyone to listen into phone calls, access emails and text messages, as well as remotely control the phone’s microphone and camera. Any similarities to Vault 7 from Wikileaks isn't just mere coincidence.
How to know if your phone is infected
Obviously, most people's first reaction when they hear this kind of news is to ask themselves: is my device infected? Keep in mind, though, that even if your device is listed it doesn't necessarily mean that its security has been compromised.
I managed to get in contact with Oren Koriat, a member of the CheckPoint Research Development Team, but I wasn't able to get more information on the details of the study before this article was published. Nevertheless, CheckPoint has provided a few tips on their website for users to follow:
- Avoid buying smartphones from stores you don't know or aren't trusted among users;
- Before buying a phone, ask to examine the device. Turn the device on, surf the web, connect to a WiFi network and so on. If you see ads that unlock the screen or ones that randomly show up, don't buy the device.
- Avoid downloading apps from unofficial and untrusted stores.
- Keep your software up to date and with the proper security patches.
An antivirus app will be able to detect whether your smartphone contains pre-installed malware
What is the most effective action in this case?
If you bought an infected device, you may not have noticed that it contained malware. Nikos Chrysaidos, the Head of Mobile Threat Intelligence and Security at Avast, recommends that you install an antivirus app to determine whether your smartphone contains pre-installed malware:
"Antivirus is the main and, in some cases, the only way to know if your smartphone is infected with malware. In many cases, like this one, malware is hidden and it runs in the background, which means that the phone's owner won't see the malware's icon in the list of running apps on their phone. This, naturally, is done so that the malware can collect personal information and stay on the device for the longest possible time without being detected."
Can smartphones leave the factory infected?
Until the opposite is proven to be true - no, smartphones can't leave the factory infected. As the CheckPoint has highlighted, there also the possibility that at some point between production and release, malware can be installed on a device by a third party.
Do you need to worry about this? Maybe. If you bought your device from an untrustworthy source then, yes.
Is there some way to check if your device is infected? Yes. If you're worried or suspicious about whether your smartphone's software is legitimate or not, install an antivirus.
Do you need to have an antivirus installed on your smartphone to be safe? Not necessarily. If you don't use untrusted sources to download apps, you don't click on pop-ups that promise huge discounts or chains in messaging apps, you'll be safe with Android.
Are you worried about the findings of CheckPoint's study? Will you be installing an antivirus in the near future? Let is know in the comments below.













About 2 or 3 years ago, i bought a galaxy tab S2. I scanned it with an antivirus app, and it was all OK. Then, my uncle has bought a Galaxy S7 and, less than a year ago, my dad has bought a galaxy S7 edge. Altough they have never noted something strange in their devices, they don’t believe that antivirus apps are useful so they have risked to buy an infected device (and I’ve risked it, too)!
So, does no editor around here intend to correct the double negative I mentioned? It's conveying precisely the opposite of what was actually intended, which would tend to make anyone who understands English not want a smartphone at all.
Hi Andria D., thanks for you comment! That phrase is fixed now, it was a error that slipped through our proofreading.
Pretty big brands named, and if the malware is non-removable (e.g. using a software tool) the OEMs ought to be volunteering or be legally forced to exchange the infected devices for new ones. Since some of the infections seem to be adware, I'd wonder if a system-wide ad blocker wouldn't neutralize them (e.g. DNS66)
The DooGee X5 Max Pro is heavily infected. The last OTA update made Chrome a system App but it is heavily infected.
I know lot of people do not see the need for antivirus/spyware apps. I think they are an absolute necessity in todays ever growing digital environment.
Totally agree Mark. I have installed and used them ever since my very first smartphone. Will I install on any future smartphone, absolutely.
Samsung Galaxy note 8 in the list and removal of Google pixels! Talk about credibility! Lol
Some really poor syntax in this article needs to be fixed, as it is conveying the opposite of what is intended: "no, smartphones can't leave the factory uninfected" -- what that clause says is that every smartphone that leaves a factory IS infected. Obviously that is not the case. The CORRECT syntax in that clause would be "no, smartphones can't leave the factory infected." It's basically a double negative, which conveys a positive.