New Stagefright security exploit puts a billion Android devices at risk


The Android security problem known as Stagefright is back, in a new and just-as-worrying form. The original Stagefright issue, which has has been causing concern for months, exploited a weakness in the Android media handler, allowing hackers to execute code through videos embedded in MMS messages. Now, a similar vulnerability has been discovered for audio files. Find out everything you need to know about Stagefright below.

A new Stagefright threat that targets Android phones through MP3 and MP4 files has been discovered. The code hides within the audio file and activates once users preview it or visit a page where the file is embedded. This audio preview function exists within most versions of Android, so nearly every Android device is susceptible to this exploit. The malicious code can also be sent to a user's phone via public Wi-Fi.
So far no infected devices have been reported. Google is currently working on a fix and says it will issue a security update in October. A rollout from individual carriers will begin soon after.
To learn more about the original Stagefright vulnerability and how to guard your phone against it, see our previous coverage below.
What is Stagefright?
Stagefright has been called the biggest Android security concern ever. It occurs when malicious code is unknowingly triggered by media in multi-media messages (MMS). Stagefright could affect a billion devices, most particularly those running Android Jelly Bean or earlier. This number, if you've taken a recent look at the percentages of different Android versions currently in use, is staggering.
Only 18 percent of Android devices are running a version of Android Lollipop and less than three percent are using Android 5.1. More than 40 percent are running Jelly Bean or earlier. (KitKat also accounts for around 40 percent of users.)
The good news is that Google has clarified that, ever since Android 4.0 Ice Cream Sandwich, a technology known as Address Space Layout Randomizing (ASLR) has been a part of Android. ASLR supposedly protects users from the Stagefright attack method because the RAM an app uses is never the same.
But the process is not perfect and nefarious attempts to circumvent ASLR are apparently already underway. Researchers have already demonstrated how Stagefright can be triggered via apps or even URLs. Fortunately those avenues require the user to manually retrieve the video, unlike MMS, which is retrieved automatically.

How do I know if I am affected by Stagefright?
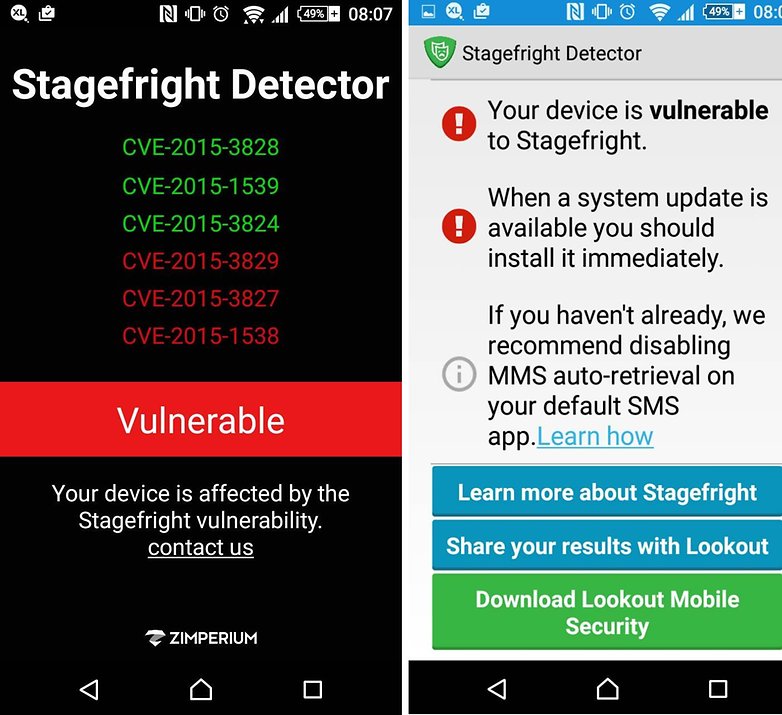
How do you know if your phone is affected? You have a couple of options. Both of the following apps will tell you if you are vulnerable to the Stagefright.
- Download Stagefright Detector app from Zimperium Inc.
- Download Stagefright Detector of Lockout Mobile Security
How do I stop Stagefright?
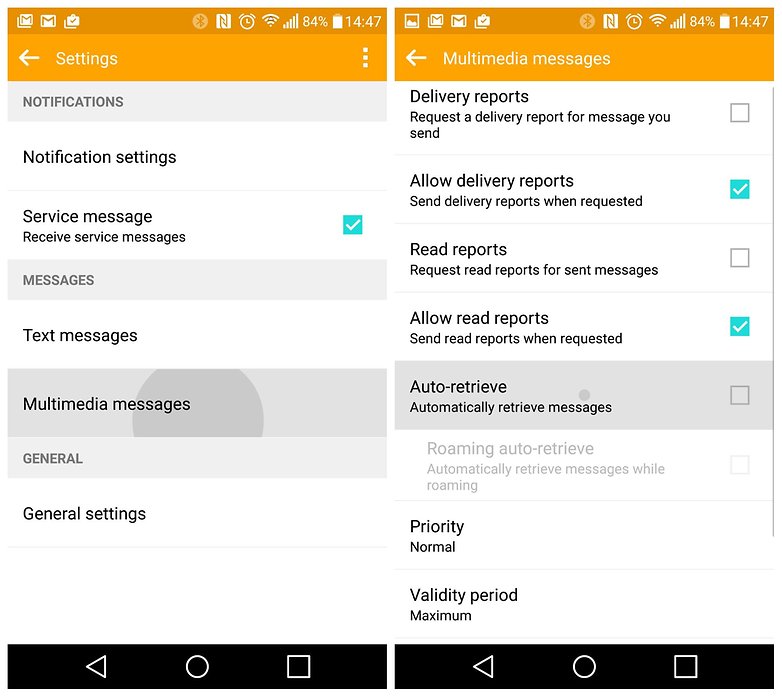
The bad news is there's not much you can do as an end-user. The current band-aid solution is to go into your messaging app's settings and turn off auto-retrieve for MMS (this goes for the default Messaging app as well as Hangouts).
You may also want to disable auto-downloads in WhatsApp. Go to Settings > Chat Settings > Media Auto-Download and make sure video auto-downloads are disabled under 'When using mobile data', 'When connected on Wi-Fi' and 'When roaming'.
Generally speaking though, steer clear of any suspicious MMS messages with videos in them, especially from people you don't know, and just hope your manufacturer and carrier get the patch out to you as quickly as possible.
As soon as you see a pending update on your device, install it immediately, and use one of the apps above to ensure you are no longer vulnerable. Of course, the apps will offer to provide you with protection if your device is vulnerable, but we have no way of telling how effective that protection is.
Which phones will get the Stagefright patch?
Several manufacturers have already announced they will issue a Stagefright patch (and several will now start monthly security updates). We've listed the manufacturers that have made an announcement below, along with any devices that have been confirmed for the update.
Google Stagefright update
Naturally, Google was the first to Android One devices have reportedly been patched already.
- Nexus 6 Android update
- Nexus 5 Android update
- Nexus 4 Android update
- Nexus 9 Android update
- Nexus 7 (2013) Android update
- Nexus 7 (2012)
- Nexus Player
Samsung Stagefright update
Samsung was also quick to issue a statement about the Stagefright patch and monthly updates for its most popular devices. Various carriers, including Sprint and AT&T, were quick to issue statements and push the patch out for the devices listed below.
Several other popular devices, including the Galaxy S4 and Galaxy S3, are apparently on the 'to-do' list for a patch, but we don't know exactly when that will come.
- Galaxy S6 Android update
- Galaxy S6 Edge Android update
- Galaxy S6 Active
- Galaxy S5 Android update
- Galaxy S5 Active
- Galaxy Note 4 Android update
- Galaxy Note Edge Android update
Motorola Stagefright update
Motorola has now joined the Stagefright chorus, announcing a huge list of devices to be patched.
- Moto X Style (patched from launch)
- Moto X Play (patched from launch)
- Moto X (2014) Android update
- Moto X (2013) Android update
- Moto X Pro
- Moto Maxx/Turbo Android update
- Moto G (2015)
- Moto G (2014) Android update
- Moto G (2013) Android update
- Moto G 4G LTE (2015)
- Moto G 4G LTE (2014)
- Moto E (2014)
- Moto E (2013) Android update
- Moto E 4G LTE (2015)
- DROID Turbo
- DROID Ultra/Mini/Maxx
LG Stagefright update
LG confirmed to Wired that it would be updating several devices and launching monthly security updates, although no official statement has yet been issued. The devices that have apparently got the fix in the pipelines include:
- LG G4 Android update
- LG G3 Android update
- LG G2 Android update
HTC Stagefright update
HTC has also pushed the Stagefright patch to several devices, but no official statement has been made on monthly security updates.
- HTC One M9 Android update
- HTC One M8 Android update
- HTC One Android update
Sony Stagefright update
Like HTC and LG, no official statement has been issued from Sony, but the following devices have reportedly been patched for the Stagefright bug:
- Xperia Z4
- Xperia Z3 Android update
- Xperia Z3 Compact Android update
- Xperia Z2 Android update
Are you affected by Stagefright? What are your thoughts on Android security issues?


















I was able to screen mirror when I bought my galaxy s6 onto my TV
Screen mirroring won't work at the moment
Any ideas as why I can't access screen mirroring
my friend's step-aunt makes $70 an hour on the computer . She has been without a job for 5 months but last month her pay was $18819 just working on the computer for a few hours. look at here
.......>>>>>>............... www.buzznews99.com
1. It's high time that Google put OHA to good use. I mean for rough example has anyone checked out OHA's last news update on their website? That's right....2011.... An alliance that's about as functional as any economic blocs = not
2. And if that can't work then the Android user base from now on should vote with their dollars very very carefully and decisively. Buy only when you really need to upgrade and only from OEMs with a steady fw/sw rollout record. You know what I mean. Just pick one lesser evil (let's face it; every Android partner OEM on Earth Samsung included prays to the planned obsolescence deity = buy a new phone, get updated faster) over the other and IGNORE the gimmicks. No use for 4K screens, dual rear cams or hell some kind of a full body scanner later on if our bread and butter data on our device are about as safe as Kim K's well lubed ass prancing around in some back alley.
Hate to say it as far as options go but it remains clear that only a Nexus is the de facto bang for buck hands down in this regard.
Of course address space layout randomization makes it almost impossible to use this exploit.
The new Asus ZenFone 2 is secure and comes with Trend Micro pre-installed (I use Trend Micro on my Toshiba Laptop as its the best Security, along with not being an ignorant Smartphone / Computer user).
I agree with EVERYONE who suggests that Google needs to work with all Manufacturera & Carriers with continued Updates offering protection from Hackers (yes Google recently sent an email to encourage Encryption , but having attended Def-Con Hacker Convention? I'm reminded that it's easy to exploit any device - even when Encryption is in use).
Finally - I don't use WhatsApp (never have, never will) as its the Microsof Outlook Express of the Smartphone (lol)!
My Moto G 2nd Gen got an update for its fix 2-3 days ago.
Protect you device from stagefright vulnarebility will you receive security update from the manufacturer.
Check it here- www.mytechalbum.com/how-toprotect-your-android-from-stagefright/
If this is so bad and hits so many android users why is this not being pushed through a bit faster?
My phone has stage fright, and its breaking my will to live :/
I have the lollipop 5.1.1 but the apps tell me I'm vulnerable. Why?
You presumably received the 5.1 update before the patch for stagefright was issued.
Can I redownload the version update? Seems silly to have to get the same versipn that I already have. 5.1.1 is suppose to be the fix.
Flash the 5.1.1 if you had it before the update and do all wipes like cache data/factory reset 3 times and don't get the updated Android version. My Note 4 Sprint already made strange things but I fixed it and I'm on 5.1.1
The Lookout app said my device is fine and the other one said it was vulnerable
Lookout contains malware itself like McAfee too.
My Nexus Devices got an OTA update last night and now all my Nexus 4/7/5 are safe.
I downloaded the Lookout application referenced in this article. When I did a restart of my phone, I goy a warning about the app and chose to uninstall.
The Lookout App is safe - how did you get a warning for this app? Do have another antivirus app installed?
Yes, I am with Verizon and they have a security app that comes with it. I also have Macafee and I have the Lookout security app installed.
My tech friends told me it's very bad that on the LG G4 devices Macafee it's pre-installed coz that security app itself it's a malware. Even the owner of that company made a video and left the company too.