Apple Passkeys: Why everyone on the Internet will benefit from it


Read in other languages:
Passwords have long been a thing of the past because they are usually boring, cumbersome and, above all, insecure. Apple announced at WWDC 2022 that it would replace them with "Passkeys", starting with iOS 16, which is tied to your account and your devices. Read our guide to find out whether this is a really secure method and what happens if you don't have an Apple device on hand.
How much time do you spend remembering your passwords? Do you create new security keys every single year and pay attention to the security strength based on the character and number sequences? Probably not, because security companies find insecure passwords far too often in their databases each year. Most passwords are too simple, are never changed, and could be cracked within a few minutes.
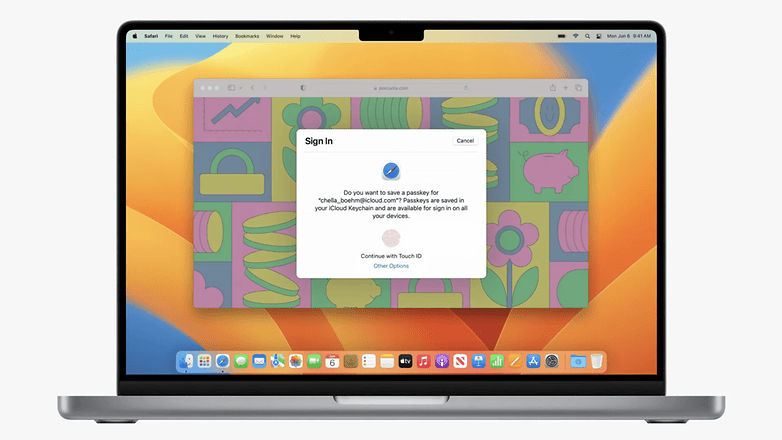
Hence, it is commendable that Apple has announced a new authentication method known as Passkeys to replace passwords. On the web, the new method is strongly linked to the Apple ecosystem, which is a shame. This is because with Passkeys, Apple merely presented its own way of dealing with the new WebAuthn credentials.
Why "Passkeys" do not only concern Apple users
You read that right. "Passkeys" are not an Apple-exclusive invention, even if it sounded like it at WWDC 2022. They are Apple's internal branding for a new type of log-in credential, which was developed by the FIDO Alliance. Apple is not part of the alliance, but according to them, it collaborated with Google and Android, among others, and follows the FIDO standards for its Passkeys. Sooner or later, almost all Internet users will benefit from the use of Passkeys.
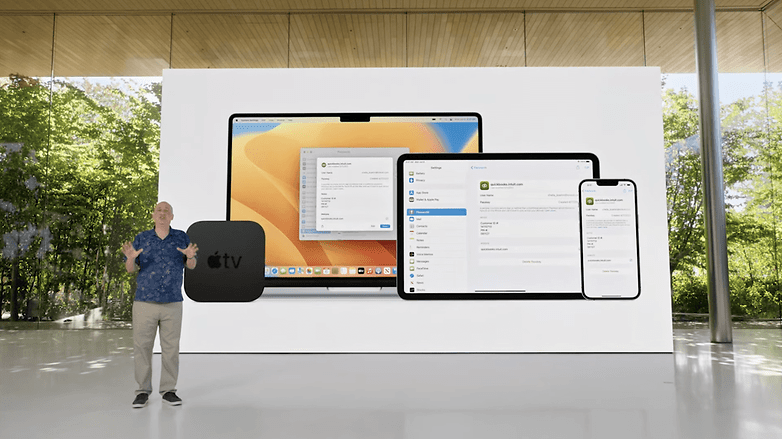
The basic idea is to implement logins using security keys rather than passwords. From the user's point of view, logins are then secured using biometric methods that enable the security keys to be compared with the server. If you are already using Face ID and Touch ID to unlock your iCloud keychain, this means very little will change in terms of accessing your accounts.
Even though today's logins on iOS are already about as convenient as the later period when Passkeys become mainstream, there is one big disadvantage. Currently, you only allow the iCloud keychain to copy your password into the login screen. From there, it is then transmitted to the server operator. There is still a risk that your passwords can be gleaned via man-in-the-middle (MITM) attacks or otherwise.
Even phishing, i.e., the scamming of passwords by pretending to be a very important emergency service or other social engineering tactics, is still possible with this method. Currently, you can easily copy passwords from your keychain and paste them into any mail if you have fallen for a scam.
This is why Passkeys and Apple's handling is so secure
Hence, in a way, using Passkeys even protects you from the proverbial danger of simply sitting in front of your display. At the very bottom of it, it is based on two security keys - a public and a private one. The public key resides on the server after setup, while the private key always remains on the device used for login. The trick lies in the mathematical formula used on which the method is based.
As Popular Science wrote, this was designed so that the private key does not have to be transmitted to the server during login attempts. This keeps your Passkey secure even in the event of MITM attacks or successful hacks on corporate servers. Passkeys are based on the WebAuthentification standard (WebAuthn), which has been used for password-less logins on the web for some time.
So if this is all already available, the question is why is everyone acting like Apple reinvented the password?
Why is everyone acting like Apple reinvented the password?
Hey, good question! What you can really give Apple credit for: They are the first to use Passkeys across devices. At the same time, they offer an application programming interface, or API, for their Passkeys. In order to enable logging in via Passkeys, websites and services must first create the prerequisites, of course. Since Apple offers its new operating systems iOS 16, watchOS 9, iPadOS 16 and macOS 13 as developer betas half a year before launch, availability at launch could already be expected across many apps and devices. In any case, Apple has already introduced its own WebAuthn credentials for WWDC 2021.
Passkeys are also firmly linked to the iCloud keychain. You can access this from any Apple device on which you have registered using your Apple ID. Since Apple uses end-to-end encryption for its keychain and does not know the security keys, the support page claims that this is a safe place for the Passkeys to reside.
The system is also protected using two-factor authentication. So if you want to register for a new Passkey, you will have to confirm this process yet again on an Apple device or via the web browser by entering a six-digit code.
Apple did not (re)invent the password-less login, but simply implemented it in a clever and secure manner. In addition, Apple devices are so widely used that Cupertino's advance will be a good incentive for services and websites to finally upgrade to WebAuthn.
Will Passkeys make it impossible to switch to Android and Windows?
Apple's move toward Passkeys still worried me a bit during the live stream, though. It strongly seemed as though Apple would once again prop up its "walled garden" with methylene. Doesn't the introduction of Passkeys make it almost impossible to use non-Apple devices or otherwise escape the Apple cosmos?
While it's not yet entirely clear how closed Apple's Passkeys integration will be, and there are three arguments against my fear.
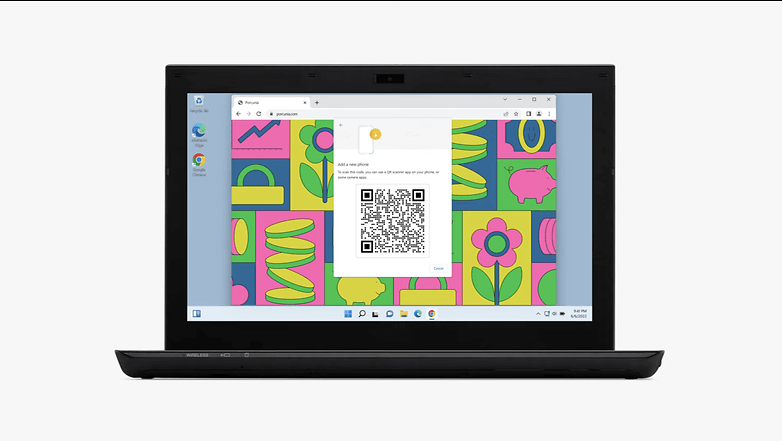
1: During the developer conference, Apple showed briefly how logins will be made possible on non-Apple devices. On the display of a Windows notebook, a QR code can be seen where it has to be scanned using an Apple device to log in. So it will be possible to log in also on Windows and Android, but you have to have your iPhone or iPad with you.
2: You can already access your iCloud keychain on Windows. All you have to do is install the iCloud app and you will see a corresponding program on your PC. Unlocking works via Windows' own authentication service known as Windows Hello, and thus also via a biometric login method. However, I doubt that this system is secure enough for Apple's Passkeys. This is because Windows relies on a PIN as a fallback, which consists of only four digits in the worst case scenario.
3:: Standard WebAuthn is, as already mentioned, not Apple's own and will certainly be natively usable with Android, Windows and other operating systems in the future. This means that you can assign new security keys for logins in order to gain access to websites. Even if they differ from Apple's synchronized keys, it does not make a difference for the handling after the setup. After all, you only log in with the fingerprint sensor or facial recognition anyway.
Conclusion: Passkeys are revolutionary, just not from Apple.
Let's summarize the developments once again. Regardless of Apple, WebAuthn will make logins on the web more secure. After far too long, our data is no longer dependent on how much time or brain power we invest in maintaining our passwords. In addition, the standard brings reliable protection against phishing, hacking, and even the type of companies that we choose to log in to.
Apple is taking a big step in this regard, becoming the first company to roll out the service across devices. At the same time, the company is taking advantage of its closed ecosystem to make logins via Passkeys a secure and convenient effort.
Apple's decision to introduce Passkeys as an important topic during its developer conference, without using its own name, is also a brilliant move. In a way, Apple is reaping the laurels that the FIDO Alliance has sown and grown in cooperation.
After all, if Android or Windows announce Passkeys support anytime soon, the public will most certainly associate it with Apple as the originator.
Touché, Apple. Touché!
Sources:



















There goes your 5th amendment protection. Law enforcement can use bio identifiers without your consent. It's too easy to abuse against the elderly with decreased brain function. And you're one accident away from being locked out of your stuff.
And now it's not just stored locally. It's out where it can get hacked and stolen. You can't reset bio identity like a password when it's stolen....
Yes, it's encrypted. But do you trust corporate encryption against the NSA and similar services?