New exploit threatens millions of Pixel and Samsung smartphones


Read in other languages:
The recent discovery of a hole in the security of the Linux kernel has sent shockwaves across the industry since countless devices are potentially affected. Among them are also newer Android phones, with two major flagship models already being demonstrated to be vulnerable to potential attacks.
TL;DR
- A new exploit named "Dirty Pipe" has been discovered in the Linux kernel.
- The security gap has existed since 2020.
- On smartphones, it mostly affects newer devices that were released with Android 12.
The "new" exploit was discovered by Max Kellerman, who managed to also demonstrate the vulnerability on a Pixel 6 and contacted Google. The so-called "Dirty Pipe" exploit allows applications that can read your files to run malicious code and can potentially give full control of your device to the attacker.
Which Android 12 devices are affected?
The exploit can be a danger to devices that use a Linux kernel of 5.8 and up. On Android, these devices primarily include newer Android 12 models like the Google Pixel 6 and the Samsung Galaxy S22 series. Knowing that the Samsung Galaxy S22 series has sold over 1.02 million devices just from pre-orders, the total number of affected devices is massive.
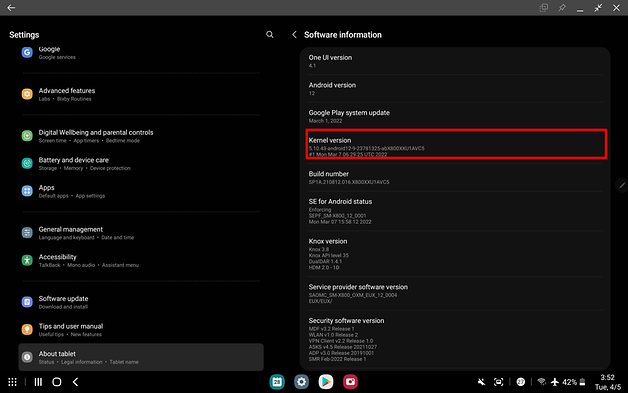
Kernel versions are not the same throughout Android 12 devices, even if they run on similar patches, so before you start worrying, we advise you to check the Kernel version.
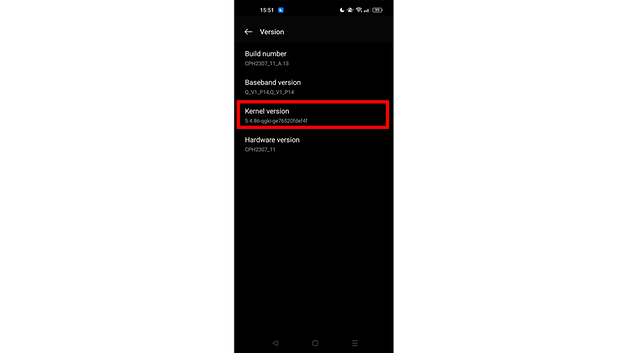
With a quick check, we were also able to confirm that the Samsung Galaxy Tab S8 Plus may also be potentially affected. On the other side, the Oppo Find X5, which also runs Android 12, runs the 5.4.86 Kernel version, so it should be safe.
- Also read: Our in-depth review of the Google Pixel 6
If you want to find out if your device is vulnerable, go to Settings and search for Kernel, and if your version number is higher than 5.8, then you may want to be a bit more cautious with the apps you download until Google releases a patch for the bug.
Google is working on it - Until then here is what you can do to keep your device safe:
Now, according to Max Kellerman's page, Google has been aware of the issue since the 22nd of February and has implemented his bug fix into the Android Kernel. But according to 9to5Google, the latest security patches for both Google and Samsung smartphones that have been released, do not mention the exploit in their patch notes, so we can not be certain if it has been appropriately addressed.
Thankfully no major attacks using the exploit have been discovered yet, but since the exploit has been disclosed to the public for about a month now, it can be assumed that malicious parties are already working on ways to utilize the exploit.
We advise users who own devices with Kernel versions above 5.8 to be a bit more aware of the apps that they download. One way to check on the permissions that an app requires before downloading it is to use the exodus security platform, which runs a test on the permissions and data gathering code of apps.
Last but not least, we highly advise users to keep their devices up to date. To check for updates, navigate to Settings > About device.
What do you think? Do you own any of the affected devices, and if yes, which one?
Via: 9to5Google Source: Max Kellerman